Tech
The Complete AV Tube Guide: Selecting, Sizing, Installing, Repairing, Maintaining, Comparing Schrader‐Valve Bicycle Tubes, and Expert FAQs
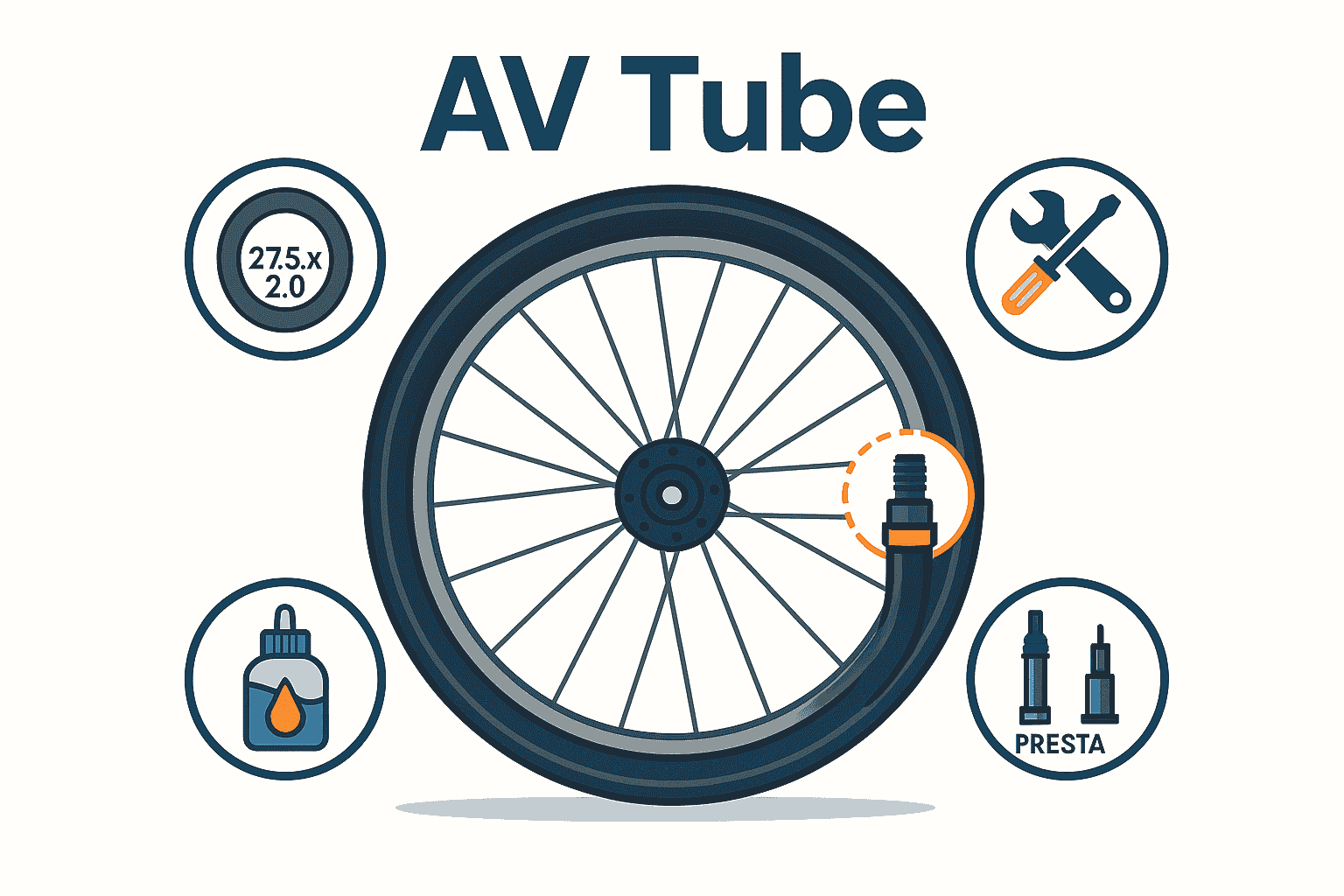
Introduction
An AV Tube is a bicycle inner tube equipped with a Schrader (American) valve—the same valve found on car tires—making it compatible with virtually all standard pumps and gas‑station air hoses. Its sturdy design simplifies roadside fixes and routine upkeep, earning favor among commuters, mountain bikers, and casual cyclists alike. In this guide, you’ll discover everything you need to know—from selecting the right tube size to mastering installation, repairs, and maintenance tips—so you can handle flats and pressure checks with confidence.
What Is an AV Tube?
An AV Tube uses a spring‑loaded Schrader valve housed in a threaded metal stem. Press an air chuck onto the valve to open the core and let air in; once you remove the pump, the valve reseals automatically. Because the core is removable, you can swap it out or inject sealant without unseating the tire. Tube packaging clearly lists compatible wheel diameters and tire-width ranges (for example, “26×1.75–2.125 AV”), ensuring an instant match for most everyday bikes.
Benefits of AV Tubes for Cyclists
The biggest advantage of AV Tubes is universal pump compatibility—no adapters required at bike shops, roadside pump stations, or gas‑station compressors. Their robust valve stem resists bending and damage, reducing the chance of leaks during emergency roadside inflation. Serviceable cores let you inject sealant through the valve to temporarily seal small punctures. Made from durable butyl rubber, AV Tubes hold air exceptionally well, while optional latex models offer lighter weight for those willing to top up more often.
Types and Sizes of AV Tubes
AV Tubes cover everything from 12″ children’s bikes to 29″ mountain and fat‑bike setups, with tire‑width options from 1.5″ to 4.0″. Packaging specifies both wheel diameter and acceptable width range, so you can quickly pick the right tube. Valve stem lengths vary—about 32 mm for shallow rims and up to 55 mm for deep‑section wheels—ensuring easy pump access. Standard butyl tubes strike a balance between cost and reliability; latex tubes shave grams but need more frequent inflation checks.
How to Choose the Ideal AV Tube
Match the tube’s diameter and width range to your tire’s sidewall markings (e.g., 700×32 C or 26×2.0). Select a width range that envelops your tire snugly to avoid over‑stretching or folding. Measure your rim depth or consult the manufacturer to determine the correct valve stem length. Everyday riders do well with budget-friendly butyl tubes, while performance‑minded cyclists might prefer lighter models. Finally, look for reinforced valve bases and trusted brands to minimize failures.
Installing and Inflating an AV Tube
Deflate the old tube completely and use tire levers to unseat one bead of the tire. Inspect the tire’s interior, removing any embedded debris that could cause new flats. Lightly inflate the new tube to give it shape, then insert the valve stem through the rim hole. Work the tire bead back onto the rim, alternating sides to avoid pinching the tube. Attach a standard pump head, inflate to the pressure range stamped on your tire, and spin the wheel to confirm an even, bulge‑free fit.
Maintaining and Repairing AV Tubes
For tiny punctures, a vulcanizing patch kit works wonders: roughen the area, apply cement, let it set, then firmly press on the patch. Larger slashes can be handled by removing the valve core and injecting sealant before reinflation. Check tire pressure weekly—too low invites pinch flats, too high risks blowouts. During tire swaps, inspect the tube for brittleness, cracks, or valve‑base wear and replace any tube that shows signs of aging. Store spares in a cool, dark spot away from sunlight and ozone sources.
AV Tube vs Presta Tube
Schrader‑valve AV Tubes feature a spring‑loaded 8 mm stem that works with most pumps right out of the box, while Presta valves use a narrower 6 mm stem and require a dedicated head or adapter. AV Tubes weigh a few grams more but offer unmatched durability and ease of use, making them ideal for everyday riding. Presta tubes shine in high‑pressure, performance‑focused road scenarios thanks to smaller rim holes and lighter weight, appealing to competitive cyclists chasing marginal gains.
Best Practices to Extend AV Tube Longevity
Always inflate to the tire’s recommended PSI to balance ride comfort and puncture resistance. Dust a thin layer of talcum powder or apply tire lubricant inside the tire before installation to reduce friction and wear. Keep rim tape intact and inspect rims for sharp spoke ends or burrs that could cut the tube. Avoid aggressive skidding, which abrades the tube against pavement. Finally, cap your valves to keep out dirt and moisture, preserving the valve core seal.
Conclusion
AV Tubes deliver a winning combination of reliability, convenience, and universal compatibility that suits a wide range of cycling styles. Their car‑style Schrader valves make inflation hassle‑free, while serviceable cores and durable materials simplify on‑the‑go repairs. By choosing the right size, stem length, and tube material, and by following proper installation and maintenance routines, you’ll maximize tube lifespan and minimize roadside headaches—so you can focus on enjoying every ride.
Frequently Asked Questions about AV Tubes
What’s the difference between Schrader (AV) and Dunlop valves?
Schrader valves feature a spring‑loaded core inside an 8 mm threaded stem, identical to car‑tire valves, and seal automatically when the pump is removed. Dunlop valves share the same stem diameter but use a replaceable inner plug (often a small ball or spring mechanism) that is unseated by pumping and inflated with Presta‑style pump heads. Modern Dunlop valves allow easy core replacement, whereas older designs relied on rubber sleeves prone to wear.
Can I use a Presta‑pump adapter on my AV Tube to fit a Presta pump?
While brass adapters exist to thread onto a Schrader stem and mimic a Presta valve, they can interfere with pressure readings and proper sealing. A better solution is to use a dual‑head pump or a reversible chuck that switches between Schrader and Presta natively, ensuring a secure fit and accurate inflation without adapters.
How do I remove and replace the core of a Schrader valve?
Use a dedicated valve‑core removal tool to engage the flats of the core and unscrew it by hand. Once removed, you can add sealant directly into the tube or inspect the core for debris. To reinstall, thread the core back in until finger‑tight, then give it an additional quarter‑turn with the tool to ensure an airtight seal.
Why won’t my pump head seal properly on a Schrader valve, and how can I fix it?
If the tire is nearly flat, the valve core’s spring may retract too far into the rim, preventing proper engagement. To fix this, deflate completely, gently pull the valve stem outward to its full length, then seat the pump head firmly while supporting the tire bead. Alternatively, use a clamp‑on or lever‑lock pump head that maintains constant pressure on the stem.
Can I convert a rim drilled for Presta valves to accept AV Tubes?
Yes. Drilling or reaming a Presta‑sized hole to the larger Schrader diameter is common on aluminum rims and does not compromise integrity for most modern wheels. This conversion allows you to use AV Tubes universally. For temporary flexibility, you can also use valve grommets or adapters, but enlarging the hole is faster and more reliable for frequent tube changes.
What should I know about using AV Tubes in a tubeless setup?
True tubeless systems require sealed rim beds and dedicated tubeless valve stems with rubber grommets. Standard AV inner tubes aren’t designed for tubeless use, but you can remove their cores and inject sealant into a tube that’s then partially seated to act as a “pseudo‑tubeless” setup. For a proper tubeless Schrader installation, use tubeless‑specific Schrader valves and ensure the rim tape is airtight around spoke holes.
Also Read:
Tech
CryptoProMarkets.net Review: Understanding Its Place in the Trading World

In the evolving landscape of digital trading, platforms that combine innovation with usability are becoming increasingly valuable. CryptoPro Markets positions itself as one of those platforms that not only offers functionality but also seeks to redefine how users engage with the digital asset world. By emphasising accessibility, tools, and trustworthiness, it has become a noteworthy contender among trading platforms. This CryptoProMarkets.net review explores the platform’s core features, usability, and what sets it apart for traders at all levels.
First Impressions of CryptoPro Markets
CryptoPro Markets is designed with a clear vision to simplify digital asset trading while maintaining a professional-grade experience. The platform integrates multiple layers of functionality, from intuitive navigation to advanced charting, ensuring that both newcomers and experienced traders can find their footing. Unlike platforms that overwhelm users with overly technical designs, CryptoPro Markets blends sophistication with clarity, making its interface approachable without compromising on depth.
Account Setup and Accessibility
CryptoPro Markets offers multiple account types tailored to different user needs. From beginners starting their trading journey to more seasoned traders looking for advanced features, the platform accommodates diverse goals. Each account tier includes specific benefits, allowing users to select the option that aligns with their trading style and aspirations.
Accessibility is another factor where CryptoPro Markets excels. The registration process is streamlined, requiring minimal steps to get started, yet it incorporates essential verification layers for added security. This balance between simplicity and responsibility makes the onboarding process efficient while maintaining compliance standards.
Trading Experience
A critical aspect of this CryptoProMarkets.net Review is the actual trading experience. The platform offers a wide range of assets for users to explore, ensuring that traders with diverse preferences can find suitable opportunities. The trading dashboard is well-designed, offering advanced charting tools, indicators, and real-time data that allow for informed decision-making.
Execution speed is another strength. Trades are processed without unnecessary delays, which is crucial in volatile markets where even seconds matter. Whether you are entering or exiting a position, the responsiveness of CryptoPro Markets gives users a sense of control and confidence.
Another notable point is customisation. Users can adjust chart styles, set alerts, and personalise their trading workspace. This flexibility allows traders to tailor the platform to their unique strategies, which is not always possible with other platforms that enforce rigid interfaces.
Platform Tools and Features
One of the hallmarks of CryptoPro Markets is the wide selection of trading tools it offers. The platform integrates live market data with advanced charting functions, allowing traders to analyse trends, study patterns, and make informed decisions. From customizable chart layouts to technical indicators, users have access to a toolkit that meets both basic and advanced analytical needs.
Beyond charting, CryptoPro Markets provides tools for order execution that are both responsive and reliable. Orders can be placed quickly, and the system is built to handle fluctuations in demand without delays. This reliability is vital for traders who operate in fast-moving markets, where even seconds can influence outcomes.
Another valuable feature is the alert system, which keeps users informed about price movements or market changes without requiring constant monitoring. By delivering updates directly, the platform ensures that traders remain connected to market developments in real time
Security and Reliability
Security is a cornerstone of any trading platform, and CryptoPro Markets places significant emphasis on protecting user data and transactions. The platform employs encryption protocols that safeguard sensitive information from external threats. Additionally, it maintains strong authentication processes to ensure that only authorised users can access accounts.
Alongside technical measures, CryptoPro Markets has developed a reputation for maintaining transparency in its practices. The platform provides clear guidelines on data handling, account safety, and transaction processes, reinforcing user confidence. In an environment where security breaches can erode trust, CryptoPro Markets’ commitment to protection makes it stand out.
Customer Support
Customer support plays an essential role in shaping user satisfaction, and CryptoPro Markets performs strongly in this area. The support team is accessible through multiple channels, offering quick responses to queries. Whether users need assistance with account setup, technical troubleshooting, or navigating features, the team demonstrates professionalism and attentiveness.
Beyond support, CryptoPro Markets offers educational resources that cater to different levels of experience. These resources help users understand both platform functionalities and broader trading concepts, making the platform not only a trading environment but also a learning hub. For beginners, these resources are especially valuable in building confidence and competence.
Mobile Trading Experience
The growing importance of mobile trading cannot be overstated, and CryptoPro Markets embraces this reality with a robust mobile application. The app mirrors the desktop platform’s functionality, offering a consistent and smooth trading experience on the go. Users can place trades, monitor markets, and manage accounts without compromise.
The mobile app is also optimised for speed and efficiency, ensuring that it remains responsive even during periods of high traffic. This capability provides traders with confidence that they can act quickly in dynamic conditions. By combining performance with design, the app delivers convenience without losing depth.
Fees and Costs
CryptoPro Markets operates with a transparent approach to fees. The platform outlines its cost structure clearly, avoiding hidden charges or complex pricing models. This openness not only builds trust but also helps users plan their trading strategies without unexpected costs.
The fee system itself is designed to remain competitive, making the platform accessible to a wide range of traders. By balancing affordability with premium services, CryptoPro Markets positions itself as a fair and user-oriented option.
User Feedback and Reputation
The first thing users notice about CryptoPro Markets is its polished and responsive interface. Every element, from the dashboard to individual trading sections, is arranged with precision, avoiding unnecessary clutter. This thoughtful design creates a smooth user experience, particularly beneficial for those who want to focus on executing trades efficiently.
The platform’s interface also demonstrates consistency across devices. Whether accessed on a desktop, tablet, or mobile phone, the design adapts without sacrificing accessibility. Such uniformity ensures that users can trade seamlessly wherever they are, adding flexibility to the trading process.
Conclusion
CryptoPro Markets emerges as a reliable, innovative, and user-centred trading platform. By addressing the essential needs of modern traders, security, usability, accessibility, and performance, it distinguishes itself in a competitive field. Whether for those just entering the digital trading space or for experienced traders seeking efficiency and reliability, CryptoPro Markets offers a compelling solution.
In a market where trust and performance matter most, CryptoPro Markets delivers both with confidence. Its dedication to continuous improvement and user satisfaction reinforces its reputation as a platform built for today’s trading environment and tomorrow’s opportunities.
Tech
Why EmergingTechs.net Stay Updated Always is Your Tech Advantage

Stay Ahead of the Curve: Why It’s Crucial to Stay Updated Always
In the fast-evolving landscape of technology, what’s groundbreaking today can become standard tomorrow. Keeping pace with these changes is no longer just an advantage; it’s a necessity for professionals, businesses, and enthusiasts alike. This article explores why it’s vital to stay informed about the latest technological advancements. We’ll show you how with emergingtechs.net, you can stay updated always, ensuring you’re never left behind in a world driven by innovation. Let’s dive into the strategies and benefits of keeping your finger on the pulse of technology.
The Competitive Edge of Staying Informed
In any industry, knowledge is power. Staying current with emerging technologies gives you a significant competitive advantage. Understanding new tools and trends allows you to anticipate market shifts and innovate faster than your competitors. This foresight is invaluable for strategic planning.
By being an early adopter or simply being aware of new tech, you can identify opportunities that others might miss. For emergingtechs.net, the goal is to help you stay updated always, turning information into a tangible asset for your career or business growth.
How Emergingtechs.net Helps You Stay Updated Always
Finding reliable, concise, and relevant information can be challenging. Emergingtechs.net simplifies this process by curating the latest news and in-depth analyses on breakthrough technologies. We filter out the noise to bring you what truly matters.
Our platform is designed for easy navigation, allowing you to find information on specific topics quickly. Whether you’re interested in AI, biotech, or quantum computing, we provide the resources you need to stay updated always.
Boost Your Career with Tech Knowledge
Continuous learning is essential for professional development. Employers value candidates who are proactive about keeping their skills current. A deep understanding of emerging tech can open doors to new roles and leadership opportunities.
Regularly reading sites like emergingtechs.net helps you:
- Speak confidently about industry trends.
- Contribute innovative ideas at work.
- Identify skills you need to develop next.
This commitment to staying informed demonstrates adaptability, a highly sought-after trait in today’s job market.
Future-Proofing Your Business Strategy
Technology disrupts business models. Companies that fail to adapt risk becoming obsolete. By monitoring emerging tech, you can identify potential threats and opportunities, allowing you to pivot your strategy accordingly.
Integrating New Solutions
Staying updated helps you recognize when to invest in new software, automation, or digital platforms. This can lead to increased efficiency, better customer experiences, and new revenue streams for your organization.
Understanding Market Shifts
New technologies create new consumer expectations. Knowing what’s on the horizon allows you to prepare your business to meet these future demands effectively.
The Role of AI and Machine Learning Updates
Artificial intelligence and machine learning are transforming every sector. Developments in these fields happen at a blistering pace. Keeping up is critical for leveraging their power, whether for data analysis, automation, or creating smarter products. With emergingtechs.net, you stay updated always on the latest algorithms and applications.
Blockchain and Cryptocurrency: Beyond the Hype
Blockchain technology offers more than just cryptocurrencies. Its potential for secure, decentralized systems is being explored in supply chain management, voting systems, and digital identity. Understanding its core principles and latest use cases can help you see beyond the hype and identify practical applications.
Navigating the Internet of Things (IoT)
The Internet of Things (IoT) connects our physical world to the digital realm, from smart homes to industrial sensors. Staying informed about IoT advancements is key to understanding the future of connectivity, data collection, and automation in both personal and professional contexts.
Why You Need to Stay Updated Always on Cybersecurity
As technology advances, so do the threats. Cybersecurity is a field where ignorance is not an option. Staying current on the latest vulnerabilities, security protocols, and threat-prevention technologies is essential for protecting personal and corporate data from increasingly sophisticated attacks.
Conclusion
The pace of technological change shows no signs of slowing down. To thrive in this environment, a commitment to continuous learning is non-negotiable. By staying informed, you gain a competitive edge, enhance your career prospects, and future-proof your business strategies against disruption. The key is to have a reliable source of information that cuts through the noise and delivers clear, relevant insights.
This is where a dedicated platform becomes invaluable. To ensure you stay updated always, make it a habit to engage with quality tech news and analysis. Explore our other articles, subscribe to our newsletter for weekly insights delivered directly to your inbox, and join the conversation by leaving a comment below. Let emergingtechs.net be your guide to navigating the future of technology, one update at a time.
Frequently Asked Questions
Why is it so important to stay updated on technology?
Staying updated helps you remain competitive, make informed decisions, and identify new opportunities for growth in your career or business. It’s crucial for adapting to market changes.
How can emergingtechs.net help me stay informed?
Emergingtechs.net curates and simplifies complex tech news, providing focused articles and analyses on key trends so you can get reliable information efficiently.
How often should I check for new tech updates?
A weekly check-in is a good starting point for major trends. For fast-moving fields like AI or cybersecurity, a daily scan of headlines is beneficial.
From Range to Woods—Why Affordable Suppressors Are Every Shooter’s Smart Investment
Tech
Smarter Business Growth Through Outsourced IT Services

Technology is no longer a side function—it’s the engine that drives modern business. Whether you’re a small startup trying to scale or an established enterprise looking to stay competitive, your IT systems are central to every operation, from communication and data storage to cybersecurity and compliance.
But here’s the challenge: managing IT in-house is expensive, complex, and time-consuming. Recruiting and training staff, maintaining hardware, and staying on top of constant technological change can pull focus away from your company’s core goals. That’s where outsourced IT services come in.
By partnering with a trusted provider, businesses gain enterprise-level expertise, predictable costs, improved security, and the ability to scale quickly—all without the headaches of running an IT department internally. In short, outsourcing IT allows your business to grow smarter, not just bigger.
Why Outsourcing IT Services Makes Strategic Sense
1. Cost Control Without Sacrificing Quality
Maintaining an internal IT department requires high overhead—salaries, benefits, equipment, software licenses, and ongoing training. For many companies, this is a huge financial burden.
- Outsourced IT services shift those costs into a predictable monthly investment.
- Businesses pay only for the support they need, avoiding unnecessary expenses.
- Providers also offer enterprise-grade tools and platforms at a fraction of the cost of buying them outright.
Example: Instead of hiring a team to manage cybersecurity, a business can rely on an outsourced provider that offers 24/7 monitoring, regular threat assessments, and incident response as part of a service package.
-
Access to Specialized Expertise on Demand
Technology changes quickly—cloud computing, artificial intelligence, advanced cybersecurity tools, and compliance regulations all evolve faster than most businesses can track.
- An outsourced IT partner employs specialists who are certified in these technologies and up to date with the latest threats and best practices.
- You’re not relying on one or two employees with limited bandwidth; you’re leveraging the experience of a full team.
Result: Your company gains top-tier skills without the cost of recruiting and retaining them internally.
-
Scalability That Matches Your Business Growth
Growth is exciting—but it also brings challenges:
- Expanding to new locations
- Onboarding remote employees
- Handling seasonal surges in workload
Outsourced IT services scale effortlessly to meet these changing needs. Instead of scrambling to hire new staff or reconfigure infrastructure, your provider adjusts services in real time, ensuring you always have the right level of support.
-
Stronger Cybersecurity and Compliance
Cyber threats are becoming more sophisticated and frequent. Data breaches, ransomware attacks, and phishing scams can disrupt business operations, damage reputations, and result in regulatory penalties.
- A dedicated IT partner provides constant monitoring, regular security audits, and rapid incident response.
- They also help ensure compliance with regulations like HIPAA, GDPR, or CCPA, depending on your industry.
Bottom line: You stay protected, and your customers stay confident in your ability to safeguard their data.
How Outsourced IT Translates to Smarter Business Growth
Freeing Leadership to Focus on Strategy
When your IT issues are handled by professionals, you and your team have more time to focus on big-picture initiatives: developing new products, serving customers better, and exploring new markets.
Boosting Productivity Across the Organization
Managed IT services proactively prevent downtime, optimize network performance, and resolve issues quickly. Employees spend less time waiting for fixes and more time doing meaningful work.
Gaining Insights for Better Decision-Making
Many outsourced providers offer performance reports and analytics, showing you exactly how your IT environment is performing and where to allocate resources for maximum ROI.
Rapid Deployment of New Technology
Want to migrate to the cloud or adopt advanced collaboration tools? Your IT partner can roll these out quickly, ensuring your business stays ahead of competitors.
What to Look for in the Right IT Partner
Not all providers are equal. To truly unlock smarter growth, look for a company that offers:
- Custom service plans tailored to your business, not one-size-fits-all solutions
- Proven track record backed by real client testimonials
- Proactive support and regular communication rather than reactive “break/fix” service
- Deep expertise in cybersecurity and regulatory compliance
Frontline, LLC, for example, has been consistently recognized as a top managed IT service provider in Los Angeles. Clients highlight their responsiveness, technical expertise, and ability to deliver reliable, worry-free IT solutions.
Real-World Results: What Clients Are Saying
- “Frontline has been our IT Service provider assisting us with hosting, security, and hardware/software solutions for many years. They have done an excellent job and are always available when needed on short notice.” — Perry Daskas, AFA Claims
- “I have dealt with many IT service companies, and Frontline ranks among the best. They have delivered the highest level of professionalism, knowledge, and expertise, while being extremely responsive.” — Elias Assaf, CEO, Nations Insurance
- “Frontline is always available to solve my technical issues quickly and effectively. Their technicians are knowledgeable and helpful every time I’ve needed assistance.” — Candice Cane, Robert Hall Taxes
These testimonials demonstrate how the right IT partner doesn’t just keep systems running—it actively supports business growth.
Conclusion
Outsourced IT services are far more than a way to save money. They are a strategic growth enabler—providing expertise, scalability, security, and efficiency that allow businesses to innovate and expand without distraction.
With a trusted IT partner like Frontline, companies gain peace of mind, stronger systems, and a foundation for smarter, sustainable growth. Instead of worrying about IT, you can focus on what truly matters: building your business and serving your customers.
Tech
Techsslash Com: Your Ultimate Guide to Technology Solutions and Innovation

Introduction
In today’s rapidly evolving digital landscape, finding a reliable source for comprehensive technology insights, solutions, and innovation updates can be challenging. This is where techsslash com emerges as a game-changing platform that bridges the gap between complex technological concepts and practical implementation. Whether you’re a tech enthusiast, business owner, developer, or simply someone curious about the latest technological trends, understanding what makes techsslash com unique can transform your approach to technology adoption.
Techsslash com serves as more than just another tech website – it’s a comprehensive ecosystem designed to demystify technology for users across all skill levels. From cutting-edge software reviews to in-depth tutorials, hardware comparisons to emerging technology forecasts, this platform has established itself as a trusted resource in the technology community. The platform’s commitment to delivering accurate, timely, and actionable content has made it a go-to destination for millions of users worldwide seeking reliable technology guidance and solutions.
What Makes Techsslash Com Stand Out in the Tech Industry
Comprehensive Technology Coverage
Techsslash com differentiates itself through its extensive coverage of technology sectors. Unlike platforms that focus on single niches, this site provides insights across multiple domains including software development, hardware innovations, cybersecurity, artificial intelligence, and emerging technologies.
The platform’s editorial team consists of industry experts, certified professionals, and experienced practitioners who bring real-world knowledge to their content creation. This ensures that every article, review, and tutorial published on techsslash com meets high standards of accuracy and relevance.
User-Centric Approach
What sets techsslash com apart is its commitment to user experience. The platform prioritizes clarity, making complex technological concepts accessible to readers regardless of their technical background. Each piece of content is crafted with the end-user in mind, focusing on practical applications rather than theoretical discussions.
The site’s intuitive navigation system allows users to quickly find relevant information. Whether you’re searching for specific software solutions, troubleshooting guides, or industry analysis, techsslash com’s organized content structure ensures efficient information discovery.
Core Services and Features Offered by Techsslash Com
In-Depth Product Reviews and Comparisons
Techsslash com excels in providing comprehensive product evaluations that help users make informed purchasing decisions. These reviews go beyond surface-level assessments, diving deep into performance metrics, user experience, value propositions, and long-term reliability factors.
The platform’s review methodology incorporates both technical testing and real-world usage scenarios. This dual approach ensures that recommendations provided by techsslash com reflect actual user needs and expectations rather than theoretical specifications alone.
Educational Content and Tutorials
One of the strongest aspects of techsslash com is its educational content library. The platform offers step-by-step tutorials covering everything from basic computer skills to advanced programming concepts. These tutorials are designed with progressive learning in mind, allowing users to build skills systematically.
Key educational features include:
- Beginner-friendly explanations of complex concepts
- Interactive code examples and practical exercises
- Video demonstrations and visual guides
- Regular updates reflecting current industry standards
Technology News and Industry Analysis
Staying current with rapidly changing technology trends requires reliable news sources. Techsslash com delivers timely updates on industry developments, product launches, company acquisitions, and technological breakthroughs that impact both consumers and businesses.
The platform’s analysis goes beyond mere reporting, providing context and implications of news events. This analytical approach helps readers understand not just what’s happening in technology, but why it matters and how it might affect their personal or professional technology decisions.
How Techsslash Com Serves Different User Demographics
Professional Developers and IT Specialists
For technical professionals, techsslash com offers advanced content including code repositories, development best practices, architectural discussions, and emerging framework analyses. The platform serves as a knowledge hub where experienced developers can stay updated on industry trends and discover new tools and methodologies.
Professional users particularly appreciate the platform’s focus on practical implementation rather than theoretical concepts. Real-world case studies, performance benchmarks, and scalability discussions provide valuable insights for professional decision-making.
Small Business Owners and Entrepreneurs
Techsslash com recognizes that small business owners need technology solutions that are both effective and budget-conscious. The platform provides targeted content addressing common business technology challenges, from selecting appropriate software solutions to implementing cybersecurity measures.
Business-focused content includes:
- Cost-benefit analyses of technology investments
- Implementation guides for business software
- Security recommendations for small enterprises
- Productivity enhancement strategies through technology
Technology Enthusiasts and Hobbyists
The platform caters to individuals passionate about technology who want to explore new possibilities and understand emerging trends. Content for this demographic includes product showcases, innovation spotlights, and forward-looking technology predictions.
Enthusiast-oriented features often explore cutting-edge developments in areas like artificial intelligence, virtual reality, blockchain technology, and Internet of Things applications, providing both technical depth and accessibility.
Quality Assurance and Content Standards at Techsslash Com
Editorial Excellence and Fact-Checking
Techsslash com maintains strict editorial standards to ensure content accuracy and reliability. Every piece of content undergoes thorough fact-checking processes, source verification, and technical validation before publication.
The platform’s commitment to quality extends beyond accuracy to include readability, relevance, and usefulness. Content creators follow established guidelines that prioritize user value while maintaining technical precision.
Regular Content Updates and Maintenance
Technology evolves rapidly, making content freshness crucial for maintaining relevance. Techsslash com implements systematic content review and update procedures to ensure that information remains current and applicable.
Update processes include:
- Regular review of existing content for accuracy
- Revision of outdated information and recommendations
- Addition of new developments to existing topics
- Archival of obsolete content with appropriate redirections
Community Engagement and Feedback Integration
The platform actively encourages user participation through comments, questions, and feedback mechanisms. This community engagement helps identify content gaps, clarify confusing explanations, and prioritize future content development.
User feedback directly influences content creation priorities, ensuring that techsslash com continues to address real user needs and interests rather than purely editorial assumptions.
Technology Categories and Specializations on Techsslash Com
Software Development and Programming
Techsslash com provides extensive coverage of programming languages, development frameworks, software engineering practices, and coding best practices. Content ranges from beginner tutorials to advanced architectural discussions.
Popular programming topics include web development, mobile app creation, database design, API development, and software testing methodologies. The platform keeps pace with evolving development practices and emerging programming paradigms.
Hardware Reviews and Recommendations
Hardware coverage spans consumer electronics, computer components, mobile devices, and emerging hardware categories. Reviews focus on performance, value, durability, and suitability for different use cases.
The platform’s hardware evaluation methodology considers both technical specifications and real-world performance, providing readers with practical insights for purchase decisions.
Cybersecurity and Privacy Solutions
Given increasing digital security concerns, techsslash com dedicates significant resources to cybersecurity education and solution recommendations. Content covers personal privacy protection, business security strategies, and emerging security threats.
Security-focused content includes:
- Step-by-step security implementation guides
- Analysis of security tools and services
- Threat awareness and prevention strategies
- Privacy protection techniques for different user types
Future Vision and Development Roadmap for Techsslash Com
Emerging Technology Integration
Techsslash com continues expanding its coverage to include cutting-edge technologies like artificial intelligence, machine learning, blockchain applications, and quantum computing developments. The platform aims to make these complex topics accessible to broader audiences.
Future content development focuses on practical applications of emerging technologies rather than purely theoretical discussions. This approach ensures that users can understand both the potential and limitations of new technological developments.
Enhanced User Experience Features
Platform development priorities include improved search functionality, personalized content recommendations, and enhanced mobile accessibility. These improvements aim to make techsslash com even more user-friendly and efficient for information discovery.
Planned enhancements include:
- Advanced filtering and categorization options
- Personalized content feeds based on user interests
- Improved multimedia content integration
- Enhanced community interaction features
Global Expansion and Localization
Recognizing its global user base, techsslash com is working toward better localization and regional content adaptation. This includes addressing regional technology preferences, regulatory differences, and market-specific recommendations.
Conclusion
Techsslash com has established itself as an indispensable resource in the technology ecosystem, serving diverse user needs through comprehensive, accurate, and accessible content. The platform’s commitment to quality, user-centric design, and continuous improvement makes it a valuable destination for anyone seeking reliable technology information and guidance.
What makes techsslash com particularly valuable is its ability to bridge the gap between complex technological concepts and practical implementation. Whether you’re a seasoned professional looking for the latest industry insights, a business owner seeking technology solutions, or an enthusiast exploring new possibilities, the platform provides content that is both informative and actionable.
The platform’s emphasis on community engagement, regular content updates, and quality assurance ensures that users receive current, accurate, and valuable information. As technology continues evolving at an unprecedented pace, having access to a reliable, comprehensive resource like techsslash com becomes increasingly important for making informed decisions and staying competitive in our digital world.
Moving forward, techsslash com’s focus on emerging technologies, user experience enhancement, and global expansion positions it well to continue serving as a trusted technology resource. For anyone serious about understanding and leveraging technology effectively, exploring what techsslash com offers is not just recommended – it’s essential for staying informed and making smart technology choices in today’s rapidly changing landscape.
Ready to explore the world of technology solutions? Visit techsslash com today to discover comprehensive reviews, tutorials, and insights that can transform your approach to technology. Join thousands of users who rely on this platform for making informed technology decisions, and take the first step toward mastering the digital tools and solutions that can enhance your personal and professional success.
Frequently Asked Questions
What type of content can I find on techsslash com?
Techsslash com offers a comprehensive range of technology-related content including detailed product reviews, step-by-step tutorials, industry news analysis, hardware comparisons, software guides, cybersecurity advice, and emerging technology insights. The platform covers everything from beginner-friendly explanations to advanced technical discussions, ensuring content relevance for users across all skill levels and interests.
How often is content updated on techsslash com?
The platform maintains a regular publishing schedule with new content added daily and existing content reviewed systematically for accuracy and relevance. Updates include fresh product reviews, current industry news, revised tutorials reflecting latest software versions, and analysis of emerging technology trends to ensure users always have access to current information.
Is techsslash com suitable for beginners in technology?
Absolutely! Techsslash com specifically designs much of its content to be accessible to beginners while still providing value to experienced users. The platform uses clear explanations, step-by-step guides, visual aids, and progressive learning approaches to help newcomers understand complex technology concepts without feeling overwhelmed by technical jargon.
How does techsslash com ensure the accuracy of its reviews and recommendations?
The platform employs rigorous fact-checking processes, technical validation by industry experts, real-world testing of products and services, source verification, and regular content audits. Additionally, community feedback helps identify any inaccuracies or outdated information, ensuring that all recommendations and reviews maintain high standards of reliability and usefulness.
Can I contribute content or provide feedback to techsslash com?
Yes, techsslash com encourages community participation through various channels including comment sections, feedback forms, content suggestions, and guest contribution opportunities. User input helps shape future content direction, identify areas needing coverage, and improve existing materials based on real-world user experiences and needs.
Does techsslash com cover enterprise-level technology solutions?
The platform provides coverage spanning from individual consumer needs to enterprise-level solutions. Business-focused content includes software recommendations for different company sizes, scalability considerations, security implementations, productivity tools, and technology investment guidance tailored to various business requirements and budgets.
How can techsslash com help me make technology purchasing decisions?
Techsslash com provides comprehensive product comparisons, detailed feature analyses, performance benchmarks, value assessments, user experience evaluations, and long-term reliability considerations. This thorough approach helps users understand not just what products do, but how they perform in real-world scenarios and whether they provide good value for specific use cases and budgets.
Techsslaash Com: Your Ultimate Gateway to Technology Excellence
-

 Tech7 days ago
Tech7 days agoRedeepseek Com: Your Complete Guide to Advanced AI-Powered Deep Search Solutions
-

 Blog2 days ago
Blog2 days agoWhy Mannacote Is the Ultimate Solution for Advanced Surface Coatings
-

 Blog5 days ago
Blog5 days agoWhat Is Ukulele History? From Hawaii to Global Icon
-

 Blog2 days ago
Blog2 days agoUSD to CAD Conversion Tips for Maximum Value





