Tech
Life2vec Coin: Unraveling Advanced Technology, Market Potential, Investment Strategies, Blockchain Innovation, Community Engagement, Economic Impact, and Future Prospects

Introduction
life2vec coin is an innovative digital asset that has rapidly emerged as a standout project in the dynamic world of cryptocurrencies. In today’s digital economy, blockchain technology is redefining the financial landscape, and life2vec coin exemplifies this evolution with its secure, transparent, and decentralized approach.
Developed using state-of-the-art cryptography and advanced data analytics, life2vec coin offers users a seamless experience in peer-to-peer transactions. It integrates smart contracts and artificial intelligence to enhance security and optimize network performance. This not only minimizes transaction delays but also ensures the utmost reliability in every operation.
The rising global interest in digital currencies has positioned life2vec coin as a noteworthy contender in the competitive crypto market. Investors and technology enthusiasts alike are drawn to its innovative features, robust technological framework, and potential for future growth.
This comprehensive guide is designed to provide complete and in-depth insights into life2vec coin—from its technological underpinnings and market potential to investment strategies, community engagement, and future prospects. Whether you are a seasoned investor or new to the world of digital finance, this article will equip you with all the necessary information to understand and appreciate the transformative impact of life2vec coin.
Understanding life2vec coin Technology
The technology behind life2vec coin is at the forefront of digital innovation. At its core, life2vec coin employs an advanced blockchain framework that ensures every transaction is recorded with absolute transparency and security. The system leverages cutting-edge cryptographic techniques that safeguard data integrity while enabling decentralized operations.
This digital asset integrates smart contracts that automate and enforce agreements without the need for intermediaries. As a result, users experience quicker and more cost-effective transactions. The architecture of life2vec coin is designed to support scalability and adaptability. It continuously evolves through regular updates and enhancements that address security vulnerabilities and optimize transaction speeds.
In addition to robust encryption, life2vec coin incorporates artificial intelligence algorithms to predict network behavior and enhance performance. This AI-driven approach not only optimizes resource allocation but also contributes to network stability during high-volume transaction periods. The technology behind life2vec coin is supported by a dedicated development community, which works tirelessly to innovate and implement new features.
By combining these advanced technological elements, life2vec coin sets a new benchmark in the crypto industry, offering users a secure, efficient, and forward-thinking platform for digital finance.
life2vec coin Market Potential and Trends
life2vec coin has captured significant attention in the global market due to its innovative features and promising outlook. The coin’s unique value proposition is anchored in its technological advancements and its ability to offer secure, decentralized financial transactions.
Market trends indicate that the adoption of blockchain technology is accelerating, and life2vec coin is well-positioned to benefit from this surge. Investors worldwide are increasingly looking towards digital assets that combine efficiency with reliability. The robust framework of life2vec coin makes it an attractive option for those seeking both short-term gains and long-term growth.
Furthermore, the coin’s integration with modern financial technologies has spurred its popularity. Market analysts have observed a steady increase in trading volumes, reflecting growing confidence in its underlying infrastructure. Emerging trends such as decentralized finance (DeFi) and digital payment systems continue to boost interest in life2vec coin.
The global community of developers and enthusiasts actively supports the coin, fostering a vibrant ecosystem that is conducive to innovation and collaboration. As the market evolves, life2vec coin is expected to capitalize on new trends, further solidifying its position as a leading digital asset. Its potential to disrupt traditional finance makes it a topic of keen interest for investors and technologists alike.
Investing in life2vec coin: Risks and Rewards
Investing in life2vec coin presents a unique blend of opportunities and challenges that prospective investors must carefully consider. The coin’s state-of-the-art technological infrastructure and strong market potential make it an attractive option for those looking to diversify their investment portfolios.
On the reward side, life2vec coin offers the potential for significant returns due to its innovative features and rapidly growing adoption rates. Its decentralized nature, coupled with the integration of smart contracts and AI-driven analytics, positions it as a frontrunner in the digital finance revolution. As more investors recognize its value, demand increases, which could drive up its market value over time.
However, like all digital assets, investing in life2vec coin carries inherent risks. Market volatility, regulatory uncertainties, and the evolving nature of blockchain technology can lead to fluctuations in value. It is essential for investors to perform thorough research and understand both the technical and economic aspects of life2vec coin before committing significant resources.
Diversification remains a key strategy, and potential investors should balance their portfolios to mitigate risks. By staying informed about market trends and technological updates, investors can better navigate the complex landscape of digital finance and make informed decisions regarding life2vec coin.
life2vec coin and Blockchain Innovation: A Deep Dive
life2vec coin is not just another digital asset; it is a testament to the transformative power of blockchain innovation. The coin leverages a sophisticated decentralized ledger system that records every transaction with impeccable accuracy and transparency.
At the heart of life2vec coin is a blockchain network that is designed to be both secure and scalable. The use of advanced encryption methods ensures that every data point remains tamper-proof, while its decentralized architecture minimizes the risk of single-point failures. This innovative approach is complemented by the integration of smart contracts, which automate transactions and eliminate the need for intermediaries.
Artificial intelligence further enhances the functionality of life2vec coin by providing predictive insights and optimizing network performance. These AI algorithms analyze transaction patterns in real-time, ensuring that the system remains efficient even during periods of high demand. The continuous evolution of the technology is driven by a proactive developer community dedicated to refining and upgrading the coin’s infrastructure.
This deep dive into life2vec coin’s blockchain innovation reveals a robust framework built to support secure, fast, and efficient digital transactions. Its pioneering technology not only addresses current market needs but also sets the stage for future advancements in the cryptocurrency sector.
life2vec coin Community Engagement and Adoption
The success of life2vec coin is significantly driven by its vibrant and engaged community. A strong community is the backbone of any digital asset, and life2vec coin has cultivated an inclusive network of developers, investors, and enthusiasts.
This community plays a pivotal role in the ongoing development and adoption of life2vec coin. Regular online forums, social media interactions, and collaborative projects allow community members to share insights, report issues, and suggest improvements. This active engagement ensures that the coin’s development is aligned with the needs and expectations of its users.
In addition, community-driven initiatives such as educational webinars, interactive workshops, and real-time support systems help newcomers understand the nuances of life2vec coin. These initiatives foster a learning environment where both novices and experienced users can benefit.
As more users participate and contribute to discussions, life2vec coin continues to evolve in a manner that is both innovative and user-centric. The feedback loop between the community and developers is essential for refining features and addressing challenges promptly. This symbiotic relationship is a key factor in the coin’s sustained growth and increasing market adoption.
life2vec coin Economic Impact and Global Influence
life2vec coin is making significant strides in reshaping the global economic landscape. Its decentralized model facilitates a more inclusive financial system, empowering users across different regions to participate in digital transactions without the need for traditional banking intermediaries.
The economic impact of life2vec coin is evident in its ability to democratize access to financial services. By enabling secure and efficient transactions, it reduces transaction costs and fosters a more transparent economic environment. This accessibility is particularly beneficial in regions with limited access to conventional banking systems, as life2vec coin provides a viable alternative for financial inclusion.
Furthermore, life2vec coin is influencing global economic trends by driving the adoption of blockchain technology in various sectors. Its robust infrastructure supports a range of applications from microtransactions to large-scale investments, thereby influencing market dynamics on a global scale.
As governments and regulatory bodies begin to recognize the potential of digital assets, life2vec coin is positioned to play a crucial role in shaping future economic policies. Its influence extends beyond individual transactions, contributing to broader economic reforms and driving innovation in digital finance worldwide.
Future Prospects and Evolution of life2vec coin
The future prospects for life2vec coin are promising as the digital asset continues to evolve within an ever-changing financial ecosystem. With ongoing technological advancements and a growing user base, life2vec coin is poised to achieve significant milestones in the coming years.
Emerging trends such as decentralized finance (DeFi) and the integration of artificial intelligence are set to enhance the functionality of life2vec coin even further. These advancements are expected to improve transaction speeds, bolster security, and expand the coin’s utility in various financial applications.
Strategic partnerships with other innovative tech firms and financial institutions will likely play a pivotal role in driving its future growth. Such collaborations can provide life2vec coin with additional resources and market exposure, further solidifying its position in the competitive crypto market.
Moreover, the proactive engagement of its development community ensures that the coin is continually updated to meet market demands and address potential vulnerabilities. This forward-thinking approach is vital for maintaining long-term sustainability and relevance in the fast-paced world of digital finance.
As life2vec coin continues to adapt and innovate, its evolution will be a key indicator of the broader trends shaping the future of global finance. The journey ahead promises exciting developments that could redefine how digital transactions are conducted worldwide.
FAQs About Life2vec Coin
What exactly is life2vec coin?
Life2vec coin is a next-generation digital asset designed to operate on a decentralized blockchain network. It functions as a cryptocurrency that leverages advanced technologies to facilitate secure, efficient transactions. Unlike traditional fiat currencies, life2vec coin enables peer-to-peer transfers without intermediaries, reducing both cost and complexity. The coin is engineered to promote transparency in every transaction, ensuring that each step is recorded immutably on the blockchain. This robust framework not only supports everyday financial exchanges but also paves the way for innovative applications in decentralized finance, ultimately providing users with enhanced control over their assets.
How does the technology behind life2vec coin ensure security?
The security of life2vec coin is built on multiple layers of advanced technology. At its core, the coin utilizes a secure blockchain architecture that records all transactions on an immutable ledger, making it nearly impossible to alter or tamper with historical data. The incorporation of sophisticated cryptographic protocols ensures that every transaction is encrypted and validated, safeguarding sensitive financial information. Moreover, the implementation of smart contracts automates the verification process, reducing human error and the risk of fraud. Additional measures, such as regular updates and community-driven audits, further enhance the coin’s overall security posture, ensuring that users can transact with confidence even in a dynamic market environment.
What sets life2vec coin apart from other cryptocurrencies?
Life2vec coin distinguishes itself through its unique combination of advanced technology and a strong focus on user-centric design. While many cryptocurrencies rely solely on basic blockchain principles, life2vec coin integrates artificial intelligence to optimize network performance and predict market trends. This AI-driven approach not only improves transaction speed but also enhances system resilience by adjusting dynamically to network demands. Additionally, life2vec coin emphasizes community engagement, fostering an ecosystem where developers, investors, and users contribute to its continuous improvement. This blend of innovation, security, and active community support creates a robust platform that stands out in the competitive landscape of digital currencies.
How can investors benefit from life2vec coin?
Investors can benefit from life2vec coin in multiple ways, making it a compelling addition to a diversified portfolio. The coin’s innovative technology and secure infrastructure provide a strong foundation for long-term growth, potentially leading to significant returns as adoption increases. Its decentralized nature reduces reliance on traditional financial institutions, offering a hedge against economic fluctuations and centralized risks. Moreover, life2vec coin’s integration with emerging trends such as decentralized finance (DeFi) opens up new avenues for earning through staking and yield farming. With a vibrant community and continuous technological advancements, investors are provided with a dynamic environment where both immediate and future benefits can be realized.
What does the future hold for life2vec coin?
The future of life2vec coin appears promising as it continues to evolve within an ever-changing digital landscape. Ongoing developments in blockchain technology and artificial intelligence are expected to enhance its functionality, making transactions faster, more secure, and more cost-effective. As global interest in decentralized finance grows, life2vec coin is well-positioned to capture a significant share of the market. Strategic partnerships, increased regulatory clarity, and a proactive development community are all factors that contribute to its positive outlook. Furthermore, as the coin expands its ecosystem, it is likely to see wider adoption across various industries, cementing its role as a key player in the future of digital finance.
Conclusion
In conclusion, life2vec coin is a groundbreaking digital asset that encapsulates the future of blockchain technology and digital finance. From its robust technological foundation and innovative blockchain solutions to its strong community engagement and significant economic impact, every aspect of life2vec coin is designed for excellence.
This guide has provided comprehensive insights into the coin’s technology, market potential, investment dynamics, and future prospects. By breaking down complex topics into easily digestible segments, we have ensured that readers gain a complete understanding of how life2vec coin is set to revolutionize the financial landscape.
As the digital economy continues to evolve, life2vec coin stands out as a beacon of innovation, promising secure, transparent, and efficient transactions. Its future remains bright, driven by continuous technological advancements and a dedicated global community. Embrace the future of finance with life2vec coin and stay informed as this digital asset reshapes the world of cryptocurrency.
Tech
The Complete AV Tube Guide: Selecting, Sizing, Installing, Repairing, Maintaining, Comparing Schrader‐Valve Bicycle Tubes, and Expert FAQs
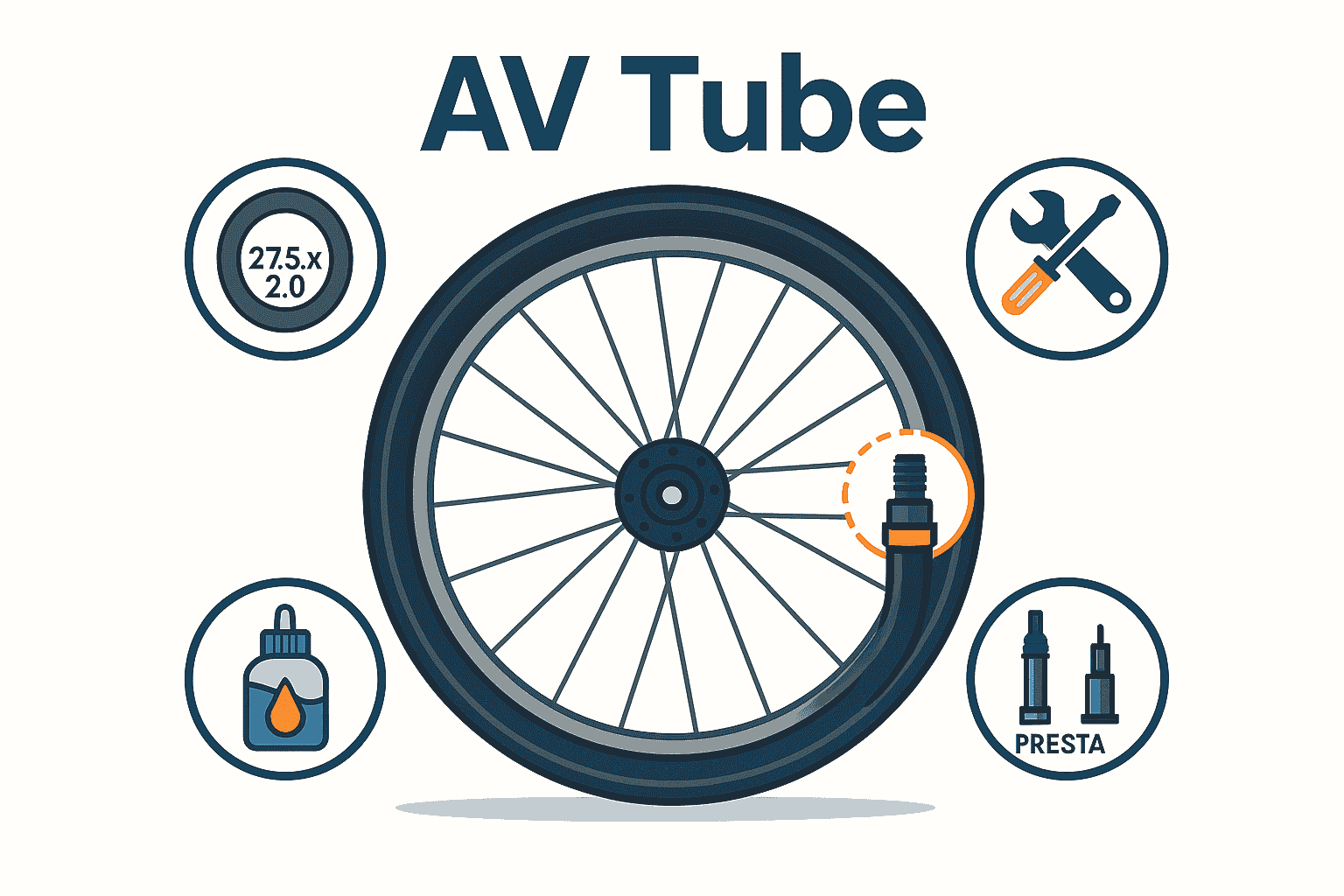
Introduction
An AV Tube is a bicycle inner tube equipped with a Schrader (American) valve—the same valve found on car tires—making it compatible with virtually all standard pumps and gas‑station air hoses. Its sturdy design simplifies roadside fixes and routine upkeep, earning favor among commuters, mountain bikers, and casual cyclists alike. In this guide, you’ll discover everything you need to know—from selecting the right tube size to mastering installation, repairs, and maintenance tips—so you can handle flats and pressure checks with confidence.
What Is an AV Tube?
An AV Tube uses a spring‑loaded Schrader valve housed in a threaded metal stem. Press an air chuck onto the valve to open the core and let air in; once you remove the pump, the valve reseals automatically. Because the core is removable, you can swap it out or inject sealant without unseating the tire. Tube packaging clearly lists compatible wheel diameters and tire-width ranges (for example, “26×1.75–2.125 AV”), ensuring an instant match for most everyday bikes.
Benefits of AV Tubes for Cyclists
The biggest advantage of AV Tubes is universal pump compatibility—no adapters required at bike shops, roadside pump stations, or gas‑station compressors. Their robust valve stem resists bending and damage, reducing the chance of leaks during emergency roadside inflation. Serviceable cores let you inject sealant through the valve to temporarily seal small punctures. Made from durable butyl rubber, AV Tubes hold air exceptionally well, while optional latex models offer lighter weight for those willing to top up more often.
Types and Sizes of AV Tubes
AV Tubes cover everything from 12″ children’s bikes to 29″ mountain and fat‑bike setups, with tire‑width options from 1.5″ to 4.0″. Packaging specifies both wheel diameter and acceptable width range, so you can quickly pick the right tube. Valve stem lengths vary—about 32 mm for shallow rims and up to 55 mm for deep‑section wheels—ensuring easy pump access. Standard butyl tubes strike a balance between cost and reliability; latex tubes shave grams but need more frequent inflation checks.
How to Choose the Ideal AV Tube
Match the tube’s diameter and width range to your tire’s sidewall markings (e.g., 700×32 C or 26×2.0). Select a width range that envelops your tire snugly to avoid over‑stretching or folding. Measure your rim depth or consult the manufacturer to determine the correct valve stem length. Everyday riders do well with budget-friendly butyl tubes, while performance‑minded cyclists might prefer lighter models. Finally, look for reinforced valve bases and trusted brands to minimize failures.
Installing and Inflating an AV Tube
Deflate the old tube completely and use tire levers to unseat one bead of the tire. Inspect the tire’s interior, removing any embedded debris that could cause new flats. Lightly inflate the new tube to give it shape, then insert the valve stem through the rim hole. Work the tire bead back onto the rim, alternating sides to avoid pinching the tube. Attach a standard pump head, inflate to the pressure range stamped on your tire, and spin the wheel to confirm an even, bulge‑free fit.
Maintaining and Repairing AV Tubes
For tiny punctures, a vulcanizing patch kit works wonders: roughen the area, apply cement, let it set, then firmly press on the patch. Larger slashes can be handled by removing the valve core and injecting sealant before reinflation. Check tire pressure weekly—too low invites pinch flats, too high risks blowouts. During tire swaps, inspect the tube for brittleness, cracks, or valve‑base wear and replace any tube that shows signs of aging. Store spares in a cool, dark spot away from sunlight and ozone sources.
AV Tube vs Presta Tube
Schrader‑valve AV Tubes feature a spring‑loaded 8 mm stem that works with most pumps right out of the box, while Presta valves use a narrower 6 mm stem and require a dedicated head or adapter. AV Tubes weigh a few grams more but offer unmatched durability and ease of use, making them ideal for everyday riding. Presta tubes shine in high‑pressure, performance‑focused road scenarios thanks to smaller rim holes and lighter weight, appealing to competitive cyclists chasing marginal gains.
Best Practices to Extend AV Tube Longevity
Always inflate to the tire’s recommended PSI to balance ride comfort and puncture resistance. Dust a thin layer of talcum powder or apply tire lubricant inside the tire before installation to reduce friction and wear. Keep rim tape intact and inspect rims for sharp spoke ends or burrs that could cut the tube. Avoid aggressive skidding, which abrades the tube against pavement. Finally, cap your valves to keep out dirt and moisture, preserving the valve core seal.
Conclusion
AV Tubes deliver a winning combination of reliability, convenience, and universal compatibility that suits a wide range of cycling styles. Their car‑style Schrader valves make inflation hassle‑free, while serviceable cores and durable materials simplify on‑the‑go repairs. By choosing the right size, stem length, and tube material, and by following proper installation and maintenance routines, you’ll maximize tube lifespan and minimize roadside headaches—so you can focus on enjoying every ride.
Frequently Asked Questions about AV Tubes
What’s the difference between Schrader (AV) and Dunlop valves?
Schrader valves feature a spring‑loaded core inside an 8 mm threaded stem, identical to car‑tire valves, and seal automatically when the pump is removed. Dunlop valves share the same stem diameter but use a replaceable inner plug (often a small ball or spring mechanism) that is unseated by pumping and inflated with Presta‑style pump heads. Modern Dunlop valves allow easy core replacement, whereas older designs relied on rubber sleeves prone to wear.
Can I use a Presta‑pump adapter on my AV Tube to fit a Presta pump?
While brass adapters exist to thread onto a Schrader stem and mimic a Presta valve, they can interfere with pressure readings and proper sealing. A better solution is to use a dual‑head pump or a reversible chuck that switches between Schrader and Presta natively, ensuring a secure fit and accurate inflation without adapters.
How do I remove and replace the core of a Schrader valve?
Use a dedicated valve‑core removal tool to engage the flats of the core and unscrew it by hand. Once removed, you can add sealant directly into the tube or inspect the core for debris. To reinstall, thread the core back in until finger‑tight, then give it an additional quarter‑turn with the tool to ensure an airtight seal.
Why won’t my pump head seal properly on a Schrader valve, and how can I fix it?
If the tire is nearly flat, the valve core’s spring may retract too far into the rim, preventing proper engagement. To fix this, deflate completely, gently pull the valve stem outward to its full length, then seat the pump head firmly while supporting the tire bead. Alternatively, use a clamp‑on or lever‑lock pump head that maintains constant pressure on the stem.
Can I convert a rim drilled for Presta valves to accept AV Tubes?
Yes. Drilling or reaming a Presta‑sized hole to the larger Schrader diameter is common on aluminum rims and does not compromise integrity for most modern wheels. This conversion allows you to use AV Tubes universally. For temporary flexibility, you can also use valve grommets or adapters, but enlarging the hole is faster and more reliable for frequent tube changes.
What should I know about using AV Tubes in a tubeless setup?
True tubeless systems require sealed rim beds and dedicated tubeless valve stems with rubber grommets. Standard AV inner tubes aren’t designed for tubeless use, but you can remove their cores and inject sealant into a tube that’s then partially seated to act as a “pseudo‑tubeless” setup. For a proper tubeless Schrader installation, use tubeless‑specific Schrader valves and ensure the rim tape is airtight around spoke holes.
Also Read:
Tech
What Is waxillgro279: From Codename and Placeholder to AI Tag, Polymer, and Digital Framework

Unraveling the Enigma of waxillgro279
The mysterious sequence “waxillgro279” triggers numerous inquiries throughout tech forums alongside research groups and social platforms. Although scholars have not discovered its actual significance, curiosity continues to grow. This article gathers all significant theories and background hints into one coherent source.
Readers can trace a well-connected answer between different elements without switching between scattered updates. We explain why some see it as an internal codename and others as discarded code residue. You will also learn how it might represent a modular digital system or an experimental sustainable polymer.
We examine whether the term is an AI-created tag or a one-of-a-kind username. This guide follows modern SEO requirements, using clear headings, relevant keywords, and semantic associations. It delivers maximum reach along with reader satisfaction.
The article contains all existing knowledge about “what is waxillgro279”. Its structured content is simple to understand and covers every angle from start to finish.
Code name origins
Technological projects within numerous companies remain out of public view through their provisional naming systems. Provisional names often use random alphanumeric codes alongside descriptive titles to conceal a project’s true purpose until official disclosure.
The name “waxillgro279” could identify a revolutionary software platform, an internal AI initiative, or a next-generation cybersecurity application still in development. The mixed letters and numbers mirror how major companies like Apple and Google label confidential projects.
Private developer discussions occasionally mention “waxillgro279”, indicating internal use rather than external branding. Once a project concludes, codenames often recycle across unrelated teams, explaining why this term sometimes appears out of context.
Should “waxillgro279” launch publicly, it will likely reappear under a different branding. Observers tracking software roadmaps and patent filings may then link this placeholder to official announcements.
Placeholder string in development
Programmers frequently insert arbitrary text into codebases during testing and prototyping stages. These “dummy data” or “placeholder strings” allow functional tests to proceed without requiring final content.
The entry “waxillgro279” matches characteristics of these placeholders: a random sequence with no semantic meaning. Reports of encountering it in logs, configuration files, and UI mock-ups reinforce that it was never meant as a final product label.
Cleanup protocols aim to remove such remnants before deployment, yet human error or automated pipeline misconfigurations can allow them to persist. When visible, placeholders may appear in error messages or settings menus, sparking user curiosity.
If this hypothesis holds, “waxillgro279” carries no special significance. It simply reflects a normal stage in the software development lifecycle that happened to slip into the public eye.
Digital framework speculation
Enterprises increasingly seek integrated platforms that unify data sources, automate workflows, and leverage AI for predictive insights. Under this lens, “waxillgro279” could denote a modular digital framework designed for these purposes.
References describe it as a container for plug-and-play modules handling tasks like data ingestion, real-time analytics, and automated reporting. Such a framework appeals to organizations needing seamless API orchestration without custom software development.
The architecture might also incorporate blockchain logging for enhanced transparency and security. If true, expect official announcements accompanied by documentation, SDKs, and sample applications.
Early adopters could trial beta versions in cloud environments or on-premise servers. Until then, scattered mentions across tech meetups suggest this concept aligns with emerging market demands.
Polymer and sustainability theory
In materials science, alphanumeric codes often label experimental compounds before marketing names are chosen. Here, “waxillgro279” may represent a novel sustainable polymer blend under development.
Researchers might combine bio-based monomers with advanced cross-linking to yield a material that degrades safely within months. Such polymers aim to replace conventional plastics in packaging and manufacturing.
Teams track metrics like tensile strength, decomposition rate, and thermal stability using identifiers like “waxillgro279” across multiple formulations. Life-cycle assessments and carbon footprint studies help evaluate environmental impact.
If this theory proves accurate, future publications or patent filings will reference “waxillgro279” explicitly, revealing its chemical structure and sustainability credentials.
Username or alias hypothesis
Randomized alphanumeric handles are common on social media, coding platforms, and gaming forums. The string “waxillgro279” could simply be a unique username chosen by an individual.
Evidence includes sporadic forum posts and repository commits tagged with that alias, without any cohesive project documentation. This pattern indicates personal rather than corporate use.
Handles like this spread across platforms, reflecting the user’s activities in open-source projects or community discussions. Spikes in search interest may follow viral content or notable contributions by the account.
Monitoring the public profiles under this name could reveal if “waxillgro279” evolves into a recognized influencer, developer, or content creator presence.
AI-generated identifier concept
Modern machine-learning pipelines often auto-generate identifiers for experiments, datasets, and resources. These tags avoid collisions with existing names and support anonymity in large-scale testing.
The pattern of letters and numbers in “waxillgro279” suggests it may be system-generated, possibly encoding date, project branch, or random seed information. It appears across various logs and data repositories, supporting this hypothesis.
When AI-driven tools produce such identifiers, they serve only functional roles within workflows. Outside that context, they hold no standalone meaning.
This case highlights how AI and automation tools shape artifacts encountered by users, sometimes sparking unexpected curiosity.
Future prospects and potential uses
As more information surfaces, “waxillgro279” could transform into a public-facing name or brand. If linked to software, expect a rebranded release with marketing materials, tutorials, and community forums.
Should the polymer theory hold, academic papers and sustainability conferences may present test results under the same identifier. Alternatively, if it remains merely an alias or internal code, it may persist as a digital curiosity.
Monitoring developer networks, patent databases, and social media channels will reveal which interpretation prevails. For now, the multiple theories illustrate its versatile role across technology, materials science, and online identity.
Conclusion
“waxillgro279” exemplifies a modern conundrum: it may be an internal codename, a placeholder string, a digital framework, a sustainable polymer, a personal username, or an AI-generated tag. Each theory draws on real-world practices in software development, materials research, and online communities.
Definitive confirmation awaits an official announcement or publication. Until then, this unified guide compiles all plausible explanations into one resource. By covering every angle, readers gain a complete understanding of “what is waxillgro279” without jumping between disparate sources.
Stay tuned to technical forums, research journals, and social platforms to discover which theory ultimately comes to light.
Frequently Asked Questions
What should I do if I encounter “waxillgro279” in a software or log file?
If you see “waxillgro279” in code, logs, or configuration files, treat it as a potential placeholder or internal identifier. First, check your project’s documentation or version control history to see if it was meant to be replaced. If it’s truly unreferenced elsewhere, flag it with your development team to ensure it’s not an overlooked dummy string before production.
How can I verify whether “waxillgro279” is a genuine product codename?
To confirm if it’s an official codename, look for references in reputable sources such as company press releases, patent filings, or authoritative tech blogs. Monitor insider forums (e.g., developer mailing lists, industry conferences) for any controlled leaks or announcements that align with “waxillgro279” details.
Where can I track updates or developments related to “waxillgro279”?
Set up alerts on developer platforms (GitHub, Stack Overflow) and use Google Alerts for any new mentions of “waxillgro279.” Following relevant hashtags on social media (like #waxillgro279) or joining niche Slack/Discord channels can also surface real-time discussions and emerging insights.
Could “waxillgro279” pose any security or compliance risks?
Since the string could be a placeholder or codename, it generally shouldn’t contain sensitive data. However, if it appears in production-facing components, verify that it doesn’t expose internal endpoints or configuration values. Conduct a security review to ensure no accidental data leakage or unauthorized access points are embedded alongside the identifier.
How do I distinguish between speculation and confirmed information about “waxillgro279”?
Evaluate the source’s credibility: peer-reviewed papers, official documentation, and recognized industry analysts carry more weight than anonymous forum posts. Cross-reference multiple independent sources before treating any claim as fact. When in doubt, label unverified theories as speculative in your research.
In what contexts might “waxillgro279” evolve into a public-facing name or product?
Should the term transition from an internal identifier to a branded release, expect it to appear in marketing materials, developer kits, or academic publications. Watch for a rebranded version in official channels—like a renamed GitHub repository, package registry entry, or trademark filing—which often signals its move into the public domain.
Also Read:
Tech
Anon Vault: A Comprehensive Guide to Secure Digital Storage, Digital Privacy, Cybersecurity Evolution, Regulatory Compliance, Integration Strategies, and Future Innovations

Anon Vault presents a system that protects digital information by guaranteeing absolute anonymity.
Modern digital life requires the most critical protection of sensitive information than it has ever needed. The concept of an anon vault operates with three interconnected features through advanced encryption technology while it also employs decentralized storage and privacy-by-design principles. The main function of anon vault systems involves secure data storage that operates under full anonymity to shield sensitive information from unauthorized access. Businesses and individual users now adopt privacy-enhanced approaches because they maintain access together with operational functionality while fighting against evolving cyber threats.
The initial segment of this paper presents an explanation of why anon vault systems hold important value in cybersecurity practices. Modern readers gain a clear understanding of security through modern encryption techniques and decentralized systems when they learn how these components support each other. An anon vault provides users with a comprehensive defense against inside attacks which protect their data from breaches along with identity theft and privacy violations. This solution fulfills regulatory requirements which include data protection laws that apply to the US and UK territories. The anon vault operates as a preemptive solution that functions as a secure storage system for digital assets to create trust in online relationships thus serving as an indispensable tool for maintaining digital privacy.
The Evolution of Anon Vault for Secure Storage
The anon vault has seen a series of technological advances as digital privacy requirements have increased throughout the modern digital environment. Digital storage systems from the early days emphasized capabilities over security features at a time when security protection was not a priority. The development of advanced tools for cyber defense occurred because cyber threats grew more complex thus requiring protective measures with both data safety and anonymity features. Contemporary anon vault systems incorporate two key features to counter recent challenges through high‑level encryption and decentralization of their architecture which defends against single point failures.
Technology innovation gave birth to anon vault solutions which addressed the problems created by increasing data breaches alongside stricter regulatory requirements. The anon vault exists now as a multi-purpose security solution which functions well within multiple digital infrastructure setups. This innovation has gained widespread adoption by organizations operating in privacy-sensitive markets especially in the US and UK to meet their requirements under GDPR and other local data protection standards. The anon vault establishes itself as a multifunctional cybersecurity tool because encryption advancements and multi-step authentication strategies continuously develop to counter new threats.
Essential in refining the anon vault have been the technical developments together with the increased user understanding and digital expertise of its platform. People who have become aware of their online privacy needs have led to an increasing interest in security solutions which conceal personal identities alongside secure data storage. The evolution demonstrates how usability and security should exist at equal levels which the anon vault realizes through its advanced technology paired with user-friendly interfaces. The anon vault transformed from an obscure technological solution into an essential digital product that fulfills modern needs of data storage.
Anon Vault and Digital Privacy: Ensuring Continuous Confidentiality
A strong integration between a digital strategy and an effective anon vault system creates vital privacy and confidentiality protection against growing digital data breach threats. Through its design the anon vault establishes two distinct data components which prevents unauthorized persons from connecting details about users to their stored information.
Digital privacy covers more than basic storage functions because it includes multiple significant aspects. The anon vault creates an effective data protection system against risks including surveillance and data abuse since it maintains both strength and user convenience. The system implements protection at various levels that uses encryption in conjunction with rigorous permission frameworks and concealed user verification systems. Users now enjoy the ability to access data using convenient and confidential systems simultaneously. Such protection allows users to maintain their digital privacy through the anon vault during unrestricted online activity.
The anon vault earns special acceptance among privacy-oriented regions including US and UK because it matches high practicality needs with robust privacy standards. Almost all jurisdictional data protection regulations are exceeded by the capabilities of the anon vault when these standards apply to the US and UK. Through the use of this technology businesses demonstrate their dedication to protecting user privacy therefore they build strong customer trust while maintaining their position as security leaders in the digital world. Anon vault represents a system beyond storage services since it offers a comprehensive solution for digital privacy which maintains transaction confidentiality constantly.
The Technology Behind Anon Vault: Cutting‑Edge Security Infrastructure
The anon vault contains three essential security components consisting of progressive encryption procedures and distributed storage networks together with active authentication technologies which form a remarkably secure infrastructure. The encryption algorithms employed by recent anon vault systems turn sensitive data into unreadable forms which prevents even targeted interceptions from identifying the content. The security of encrypted data increases through decentralized methods that distribute content among various nodes because this decentralized approach eliminates the danger of one central point of vulnerability.
The development of the anon vault depends on modern technological advancements. The integration of blockchain technology becomes an ongoing research and engineering effort to build these systems since blockchain ensures unalterable records that provide data verification. The dual encryption and decentralization method delivers both established security tools and upcoming security concepts which maintains user protection during ongoing digital threats.
Due to its advanced technology foundation the anon vault stands well-protected against current cyber security risks. The dual advantage of this solution comes from its anonymous data protection system that still enables secure access. Digital users can use their devices without fear of data breaches because the anon vault system provides complete freedom for online activities. The solution was engineered to adjust according to organizational requirements which makes it suitable for all types of users ranging from single people to large businesses. The anon vault establishes new data security standards through its combination of advanced technology with strict security protocols that transform digital protection in dynamic environments.
Anon Vault and Regulatory Impact: Navigating Legal Requirements
The adoption of a properly executed anon vault system creates significant effects on businesses that must comply with multiple regulatory requirements. Tightening data protection legislation now forces businesses across US and UK territories to implement secure privacy‑oriented data protection solutions due to strict compliance standards. The anon vault solves these problems through its design of encrypted decentralized storage which makes businesses less vulnerable to data privacy law violations.
Digital transaction policies from regulatory organizations mandate that personal information exposure needs to be kept at a minimum. The anon vault reaches maximum security by dividing user identities from encrypted distributed data stored securely on multiple nodes. The setup meets the requirements of GDPR alongside state-specific privacy rules because PII remains inaccessible in centralized databases. Modern cybersecurity strategies now heavily depend on the anon vault because organizations need this solution to fulfill regulatory requirements.
The implementation of an anonymization vault within organizational networks brings both regulatory compliance benefits as well as decreased financial risks and increased customer loyalty. Organizations must prioritize this practice because privacy breaches often create substantial financial impacts and erosion of company reputation in current market conditions. The adoption of an anon vault enables companies to lead data privacy protection activities which results in consumer trust alongside regulatory compliance. Current legal standards find their match and exceed their requirements through the implementation of an anonymous storage solution which creates a vital tool for modern data security strategies.
An organization must implement Anon Vault as part of their total cybersecurity approach
Well-established organizations need to implement anon vault as part of their complete cyber defenses for obtaining optimal data protection. The implementation process starts with system analysis to adjust anon vault technology toward full compatibility with existing technology frameworks. The combination of traditional cybersecurity approaches with innovative anonymizing techniques through the design of an appropriate strategic framework enables the anon vault to provide stronger defense against new security threats.
The first step of establishing an anon vault requires organizations to define their specific security demands. The evaluation process of existing digital systems leads to identification of optimal storage encryption solutions. Standardized APIs and secure protocols serve to connect the anon vault to the system which promotes compatibility with all platforms. The system integration process receives backing from systematic employee training along with periodic security audit procedures to enable all stakeholders optimize their use of the tool.
The successful implementation of an integration strategy includes both scalability features and flexibility elements. Organizational needs development alongside advanced cyber threats enable the anon vault to be modified and restructured without interfering with operational business continuity. The proactive strategy both strengthens organizational security measures together with building readiness against future security challenges. When an organization incorporates the anon vault into its cybersecurity approach it establishes both trust-based operations and resilience through full protection of all its digital information.
The evaluation establishes Anon Vault as a superior alternative to conventional storage methods
Traditional storage methods have distinct differences from an anon vault technology which delivers specific distinct advantages. Data repositories used in traditional storage systems have operated in centralized facilities thus exposing all sensitive content to potential unauthorized access alongside data breach risks. The decentralized nature of the anon vault framework decreases stored information vulnerability because it deploys a decentralized approach. Digital privacy transformation involves more than technological migration because it means adopting a new philosophy for privacy security.
The anon vault enables data anonymity through advanced encryption methods as it provides users secure and flexible access to stored information. Traditional systems maintain single-point access systems yet this presents a major risk because data loss becomes a systemic failure. When data spreads across various nodes of the anon vault system attackers face increased difficulty in executing complete dataset breaches. A distributed security system remains vital for modern times since cyber attackers stay busy perfecting their attacks on centralized data systems.
The anon vault design enables innovative antiterrorist improvements of security protocols while most traditional storage systems normally do not include these updates. The shift to an anon vault provides organizations with immediate security enhancements while structuring them to face anticipated digital threats in the developing digital environment. The anon vault demonstrates superior protective capabilities than common approaches because it delivers enhanced compliance with modern privacy standards together with innovative solutions for organizations that strive to protect their sensitive data.
Future Trends in Anon Vault Technology and Innovation
Technology progress within anon vaults continues to expand promisingly because of digital world development. Through continuous research and development of encryption and distributed ledger technology together with artificial intelligence capabilities both user experience and security features of anonymized vaults are expected to improve. The anon vault plans to evolve through efforts to integrate updated risk evaluation systems with automatic encryption management and advanced ways to authenticate users while dealing with modern sophisticated cyber threats.
The anon vault will develop two major features in upcoming years according to industry experts and experts. These enhancements will focus on interface usability with more user-friendly features as well as expanded scalability to reach a larger audience. An anon vault has already gained the attention of American and UK companies because they recognize its advantages for satisfying formal regulatory obligations. Advancements in research investigations will lead to fundamental changes in how digital privacy can be maintained because demand is increasing. Additional security enhancements built by these solutions allow organizations to protect their data better while maintaining their position in front of evolving cyber threats within the dynamic digital environment.
The author predicts that the anon vault will function as the key driver behind the future of cybersecurity development. Anon vault technology will achieve higher protective capabilities as developers continue their enhancements while adding more artificial intelligence components to threat detection systems. The new developments will give users and organizations abilities to defend their digital contents with full confidence and assurance of security in a digital landscape that maintains both innovation and privacy nesta.
Conclusion: Embracing the Comprehensive Benefits of Anon Vault
The anon vault operates as a revolutionary solution which addresses current digital security needs in modern complex networks. This security solution extends maximum defense through encryption algorithms which combine decentralized file storage systems together with features protecting user privacy at the user-initiated level to fulfill today’s sophisticated data security requirements. An integration of an anon vault within digital strategies provides organizations protection against cyber threats alongside compliance with shifting regulations in both US and UK markets.
The anon vault applies a cybersecurity strategy that tackles present security needs together with features which adjust to evolving threats ahead. Any individual who wishes to achieve complete digital protection alongside resistance needs this essential security tool. Users who adopt this advanced security measure gain digital confidence to handle their information securely because the system operates with one of the most secure platforms currently in use.
FAQs on Anon Vault
What is an anon vault?
An anon vault represents a protected digital storage system with top-rated encryption together with decentralized architecture to fully conceal user data.
The data privacy features of an anon vault function through what mechanism?
Anon Vault creates multiple levels of encryption protection which uses restrictive access procedures together with information isolation techniques designed to protect privacy.
The main technologies which enable an anon vault to function include decentralization along with advanced encryption?
State-of-the-art encryption together with blockchain principles and dynamic authentication protocols make up powerful security features of Anon vaults.
An anon vault fulfills what regulatory requirements?
The system safeguards personal information by using encryption protocols to maintain standard compliance as per GDPR regulations.
The user base which can take advantage of anon vault services consists of what population?
The privacy-focused markets in US and UK value this storage solution because it provides them with safe and anonymous data storage capabilities.
Users should expect which kind of evolutions in anon vault technology will emerge in upcoming times?
Modern threat detection systems derived from AI will work together with improved scalability functions while integrating better with ongoing cybersecurity standard development.
Also Read:
Tech
Vault Opener NYT Crossword: A Comprehensive Guide to History, Strategies, and Cultural Impact

Introduction
Crossword enthusiasts find attraction in the evolving world of puzzle solving because the nyt crossword vault opener stands as an intriguing challenge for them. The guide establishes comprehensive instructions for solvers at all experience levels as it examines the entire range of New York Times published vault opener puzzles. Advanced puzzles combine analytical problem-solving skills with creative thinking elements in order to require participants to solve thematic and clue-based riddles. This exploration examines the historical progression of these puzzles and their special solving methods together with their contemporary advanced techniques alongside patterns which occur frequently and their relation to cultural settings. The content divides itself into short well-organized sections which both simplify comprehension and supply complete information throughout the full article. The sections below include headings that both seamlessly include the keyword alongside strict semantic SEO principles to deliver thorough content and successful reading.
The NYT Crossword featuring the Vault Opener demands proper comprehension among players.
A serious mindset accompanies the word puzzle known as the “vault opener nyt crossword” which presents multidimensional complexity to its participants. Its creators designed this system to challenge solver understanding through veiled messages together with complex word-based riddles. Puzzle constructors put great effort into creating each clue because they serve as encryption keys which expose more hidden layers inside the grid while requiring the solver to solve puns and anagrams together with homophone devices and other cryptic elements. The artistic puzzle logic necessitates operational intelligence alongside imaginative thinking to produce an improved solving journey.
Enthusiasts of the vault opener nyt crossword find pleasure in its challenging difficulty that alters the typical crossword experience. The main obstacle surpasses standard answer recognition because it demands an interpretation of the intentional word games hidden within the clues. An exceptional aspect of each puzzle clue functions both to complete the grid addition and reveal multiple elements of secret narrative themes. Every solved letter of the puzzle functions in dual roles both to solve specific grid spaces and to create the overall narrative design of the puzzle.
Experts spend many hours on designing each of these intellectual challenges. Every clue in a puzzle undergoes multiple trials from makers until they produce the most effective combination between difficulty levels and word clarity. The developers dedicate meticulous effort to create intricate puzzles that challenge readers without being dishonest which achieves a sense of accomplishment for each successfully solved clue. Working on a vault opener nyt crossword puzzle develops problem-solving abilities while presenting language in distinctive ways that strengthen enthusiasts’ appreciation for it. Adopting the mindset of these crosswords requires an experience which surpasses simple puzzle completion because it teaches players to better understand linguistic specifics and their logical structures.
Historical Development of Vault Opener NYT Crossword Puzzles
Experts have observed the evolution of the “vault opener nyt crossword” since its inception via decades of puzzle creation under changing cultural landscapes. Crosswords began as simple word games until puzzle expertises increased causing clue difficulty to rise. Accepting traditional word match solutions was insufficient so the vault opener approach entered the world. Throughout the years puzzle makers progressively developed secret meanings and complex word-based methods to produce challenges that only veteran solvers could solve.
The New York Times has throughout history led the way toward supporting revolutionary crossword puzzle approaches. The expanding demand for advanced intellectual puzzles resulted in creators developing fresh types of crossword clues. The vault opener nyt crossword established itself as an individual puzzle category because its clues serve simultaneously as the necessary encryption to solve various component parts within the one grid. The creators built each clue to carry two purposes which boosted the overall puzzle resolution process. Such modifications mirror extensive shifts in the way people think and the way their cultural preferences develop. Users of puzzles moved away from basic word definitions because they desired challenges that required intellectual acuity and mental flexibility.
Key members of the puzzle construction industry started examining different approaches for creating clues by using puns and word reversals together with anagram puzzles. Through these approaches solvers acquired multiple meanings which needed structured analytical problem solving beyond basic word learning. The vault opener nyt crossword has developed into a contemporary symbol representing the perfect union between artistic creation and intellectual mental exercise. The historical development of crossword puzzles motivates modern creators to combine conventional methods with modern concepts thus sustaining the active nature of the field.
Strategies and Techniques for Solving Vault Opener NYT Crossword
A solver of “vault opener nyt crossword” needs more than lexical proficiency because they need technical problem-solving methods to decipher the layered cryptic clues in the puzzle. A productive problem-solving method leads by transforming each clue into its base elements. The real challenge becomes clear to solvers when they analyze both the wording flow and punctuation and the overall puzzle structure. Solvers must find concealed word transformations and instructions in this puzzle type because these masked elements remain out of sight to typical readers.
The first step in solving the clue successfully involves the detection of any irregular wording patterns or hidden word missing within the clue. Many contestants enhance their success probability by dividing clues into manageable segments to reveal hidden wordplays and anagrams that point to the solution. It is essential for solver to search for recurring pattern formats inside the vault opener nyt crossword. The word game uses unique patterns which implement hidden meanings alongside unexpected non-linear logic features to modify the typical solving approach. Writing different interpretations of clues down as part of a systematic approach provides strong benefits to solvers.
The validation of potential solutions becomes possible through answering intersecting clues in the framework. When solving these puzzles solving requires lateral thinking where a short break or reshaping our thinking pattern might help resolve stubborn clues. Advanced players solve crosswords through their innate understanding and vast knowledge of the language alongside verification by outside crossword platforms as long as they respect the puzzle conventions. The mastery of the vault opener nyt crossword requires both trial and error experiments with steady learning of new approaches. The disciplined yet imaginative puzzle-solving method improves total performance quality and strengthens understanding of sophisticated clue creation techniques.
Common Patterns and Trickery in Vault Opener NYT Crossword Clues
The “vault opener nyt crossword” puzzle gained its popularity through unique structural elements as well as its deceptive clue approaches. Puzzle constructors utilize their skill in misdirection by concealing genuine meanings of familiar words that appear in their clues. The dominant approach in vault opener nyt crosswords uses double entendres that create different meanings from a single word or statement. The method forces solvers to move past direct interpretations since it requires them to explore new definitions and relationship frameworks.
The anagram technique is commonly applied to puzzles by reshaping words until they create the solution. The process of solving these types of word puzzles requires attention to signals which will lead to letter rearrangement instead of direct interpretation. The word loop designs and pun systems appear frequently throughout these challenging puzzles. The vault opener nyt crossword utilizes reversals as a method to increase difficultly by making clues read backward. Clues are also hidden within spacing and specific punctuation marks that serve as exclusive indicators for puzzle solutions. Those who solve puzzles need to focus on the tiniest elements because stray commas or configuration-breaking line spaces can reveal understanding.
The clues intentionally lead solvers into taking logical guesses at first which get adjusted through word crossings within the puzzle grid. Each clue in a vault opener nyt crossword presents multiple levels of complexity which demands analytical observation for correct solution. Home solvers start to identify recurring pattern elements in the puzzles as they advance and these patterns help them solve following challenges. The proficiency of speed and accuracy in solving crossword puzzles increases when one knows what common crossword elements exist. Through their mixed nature between planned and unknown elements these puzzles turn basic crosswords into thought-provoking intellectual activities that deliver fulfillment as well as educational value.
Advanced Methods for Mastering Vault Opener NYT Crossword
Advanced solvers who address the “vault opener nyt crossword” employ multiple innovative problem-solving techniques that unite old methods with contemporary approaches. The process of deep analysis of clue structure forms one approach to solving the puzzle. Experts examining clues go beyond immediate answers by analyzing all elements and parts of the information provided. They interpret the language structure and components alongside hidden meaning in the writing to extract any covert commands from verbalization. Through deliberate evaluation solvers discover concealed details within the clues which later leads them to improve their response.
The advanced method of associative thinking establishes meaning connections between ideas which seem to have no relation. Different aspects of a clue reveal connections to each other which lets puzzle solvers forecast the intended direction. The vault opener nyt crossword serves as an intellectual challenge since historical information and literary knowledge as well as industrial terminology act as tools for puzzle completion. Highly experienced solvers maintain either written or mental records of the linkages they discover across puzzles which they update accordingly with each new crossword.
When solving part of the crossword grid solvers must consider the intersecting letters which already have answers to determine which clues fit best. This approach both verifies answers that seem promising and reduces the potential answers available for future clues. Advanced crossword solvers split their approach between making intuitive leaps followed by performing ordered examinations as they transition between unstructured brainstorming periods and structured evaluation procedures. Users of online forums and puzzle clubs along with discussion groups develop superior approaches through experience sharing because members discover hidden techniques. The mastery of vault opener nyt crossword at its advanced level creates a thoughtful process which turns each puzzle into an educational activity for learners to appreciate while building skills of adaptation and progress.
The Cultural Impact and Community of Vault Opener NYT Crossword
The “vault opener nyt crossword” creates a major cultural effect on a worldwide community of players who love this intellectual activity. tual strength and imaginative gameplay made this crossword type develop into an artistic form above traditional puzzles. Members of online discussion forums together with social media groups alongside local puzzle clubs(TreeNode) unite to exchange tips yet also tales of fun and achievement alongside tales of obstacles that made them frustrated. Crossword puzzles provide a unifying space for individuals from all walks of life—both pupils and people in various professions—because they share an affection for brain-teasing experiences.
The cultural significance of the vault opener nyt crossword plays a fundamental role. The vault opener nyt crossword puzzle serves as an academic research subject in discussions of problem-solving methods and creative thinking and this topic hosts workshops and symposiums focused on innovative puzzle design. Through this type of puzzle we learn language capabilities extend beyond practicality when it brings fun and complexity while leading readers to argue about unclear hints and slick traps. The structure of these puzzles provides a necessary remedy to digital speed challenges because they demand focused attention while requiring sustained effort. People who solve these puzzles regularly benefit from enhanced mental capabilities and develop a bond with others who share this same intellectual interest. The vault opener nyt crossword maintains its ability to inspire variety of participants through challenging experiences as it fosters an enduring environment for intellectual exploration and analytical thinking.
Final Reflections on the Vault Opener NYT Crossword Experience
Understanding and solving and admiring the “vault opener nyt crossword” takes readers on an ongoing path of discovery and mental satisfaction. The article has investigated all phases starting from complex clue development during history to advanced solving methods which verifies that crosswords extend past vocabulary tests. Linguistic creativity and strategic thinking are two pillars which make crosswords a celebration. People who take part in vault opener nyt crossword puzzles join an established practice which challenges their thinking abilities and strengthens their problem-solving capacity while connecting them to an active community of intellectual enthusiasts.
All the power behind these puzzles originates from their successful unification of artistic concept with reasoning. Every puzzle piece represents a well-planned adventure specifically designed to give persistent players unexpected language experiences. Customers seeking entertainment through crosswords should try the vault opener nyt because they will find an experience that continues long after the puzzle is solved with its rewarding intellectual benefits. Those who accept this challenge discover their increased respect for the craft thanks to the way problem-solving links information with instinctive thinking and creative imagination. The solving experience remains a personal accomplishment that also represents a group achievement which constantly attracts enthusiasts worldwide.
Frequently Asked Questions
Direction to a vault opening in the New York Times crossword puzzle appears here.
The New York Times crosswords include a special puzzle element which demands multiple interpretive steps to uncover hidden contents throughout the grid.
The characteristics which make vault openers stand out from standard NY Times crosswords.
To solve these types of clues readers need to merge straightforward analysis with imaginative reasoning because they demand extra analytical effort beyond basic cluing methods.
The solution for succeeding in vault opener NYT crosswords relies on which strategies?
The accuracy of puzzle solutions increases greatly through planning which consists of breaking down clues and recognizing patterns and making sideways connections.
What methods can I use to enhance my strength when dealing with these brain teasers?
Through practice along with membership in puzzle clubs and online forum interaction solvers enhance their puzzle solving methods while gaining mutual experience.
Who created the puzzles featured in these clues?
Experienced crossword constructors constantly develop new innovations by adding vault opener clues into their signature constructions because of their exceptional puzzle design abilities.
What are the available resources where I can learn about NYT crosswords that use vault openers?
Multiple resources including online communities and dedicated crossword blogs and official New York Times archives give complete practice materials and vast learning opportunities.
What are the chances of beginning NYT crossword players succeeding at vault opener puzzles?
New observers who commence with basic puzzles then proceed to intricate strategies will establish the abilities needed to resolve such complex clues.
Also Read:
-

 Tech4 days ago
Tech4 days agoAnon Vault: A Comprehensive Guide to Secure Digital Storage, Digital Privacy, Cybersecurity Evolution, Regulatory Compliance, Integration Strategies, and Future Innovations
-

 Uncategorized6 days ago
Uncategorized6 days agoHotwife Stories Unleashed: A Comprehensive Guide on Evolution, Empowerment, Communication, Boundaries, and Modern Relationship Dynamics
-

 Tech2 days ago
Tech2 days agoWhat Is waxillgro279: From Codename and Placeholder to AI Tag, Polymer, and Digital Framework
-

 Blog2 days ago
Blog2 days agoSeirei Mod Hikke Guide: Spirit Summoning, Features, Installation, Mechanics, Customization, Compatibility, Community & Updates